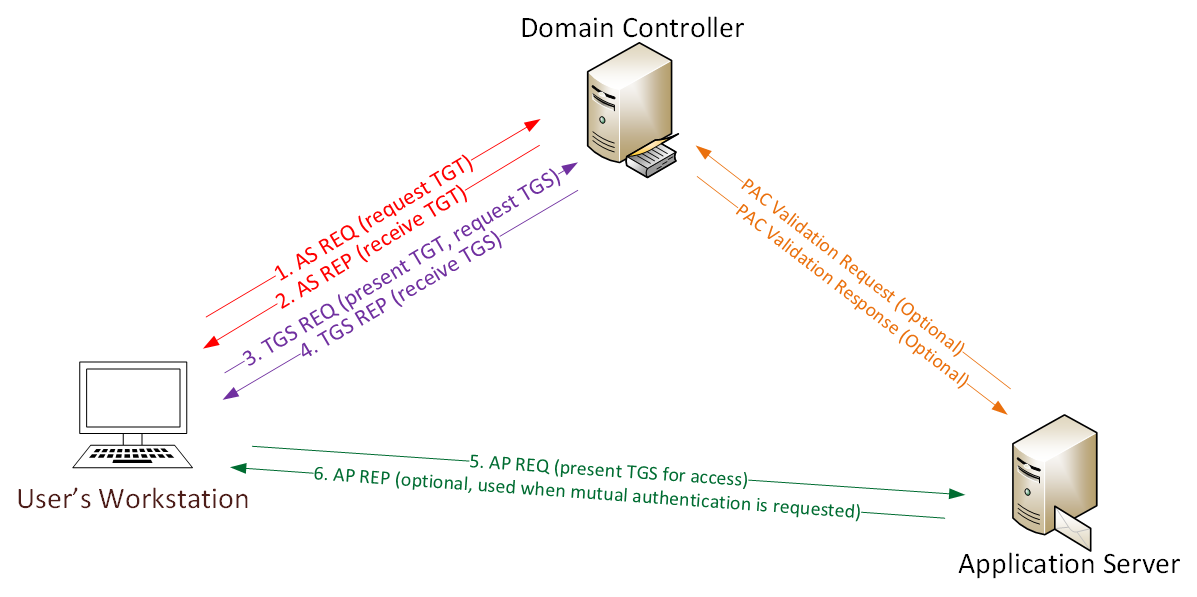
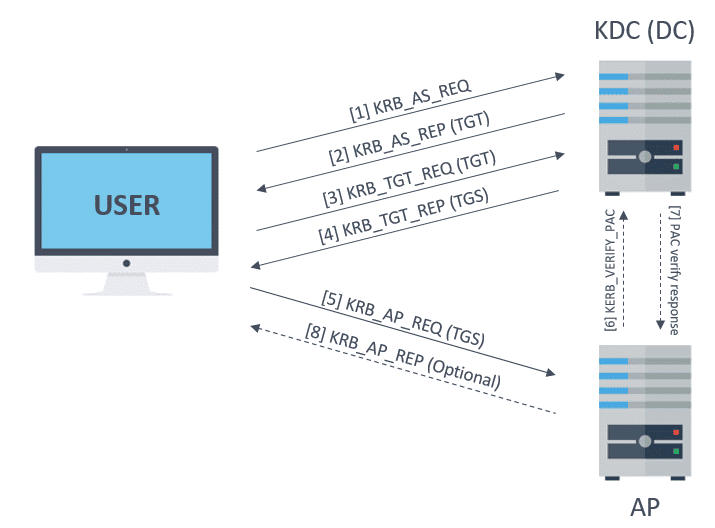
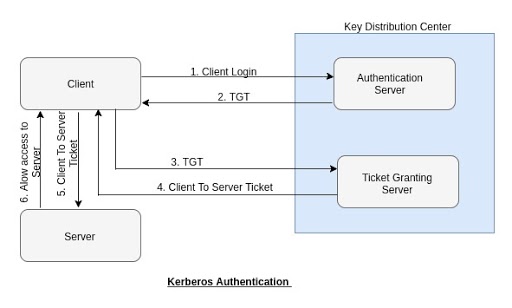
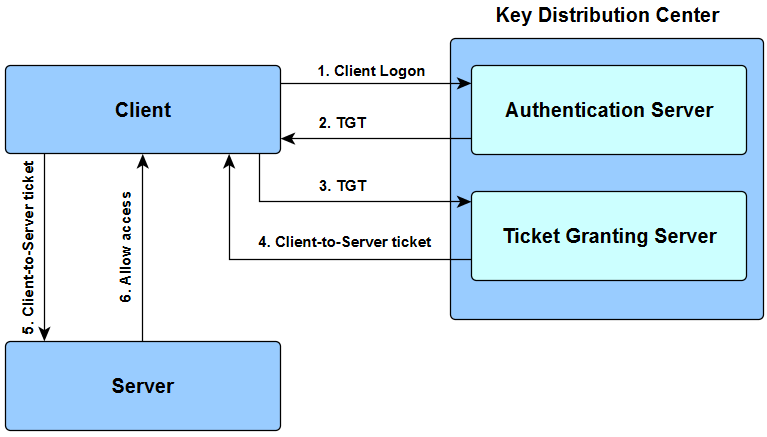
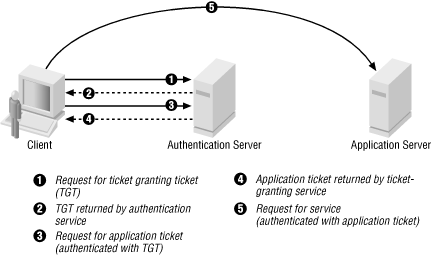
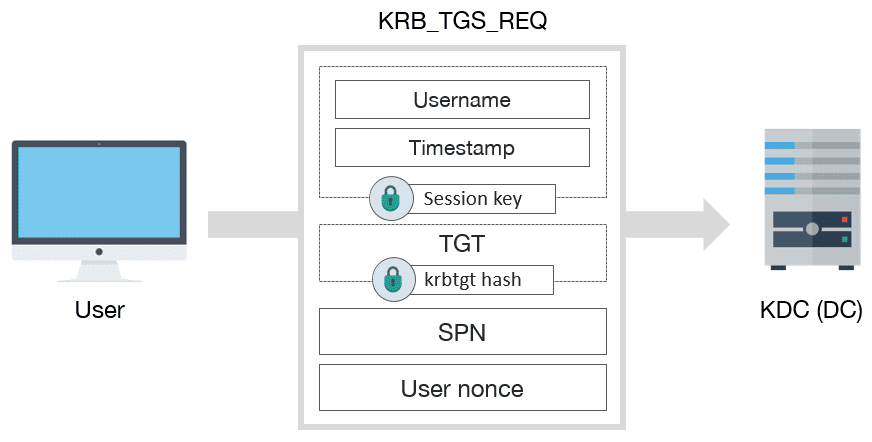
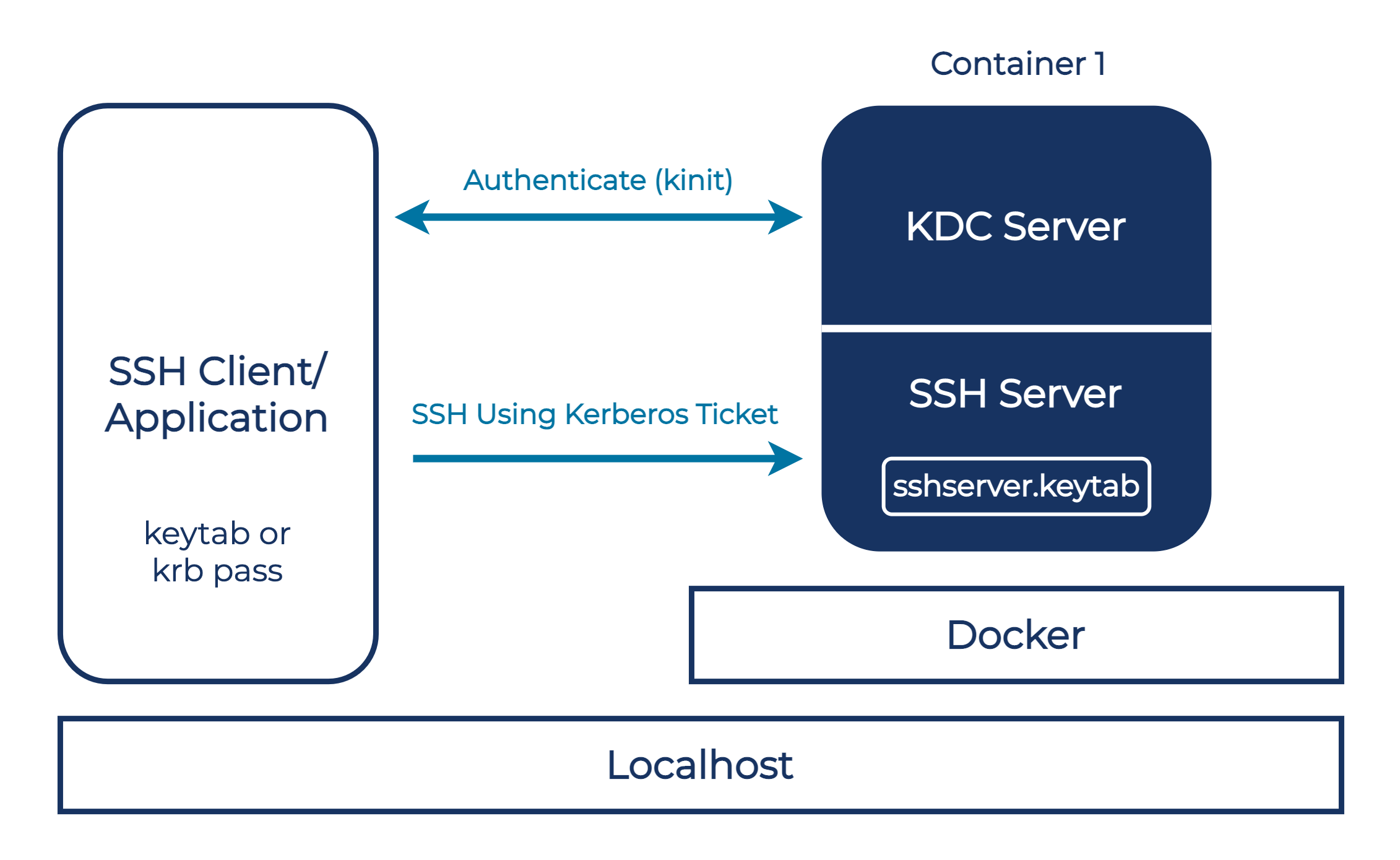
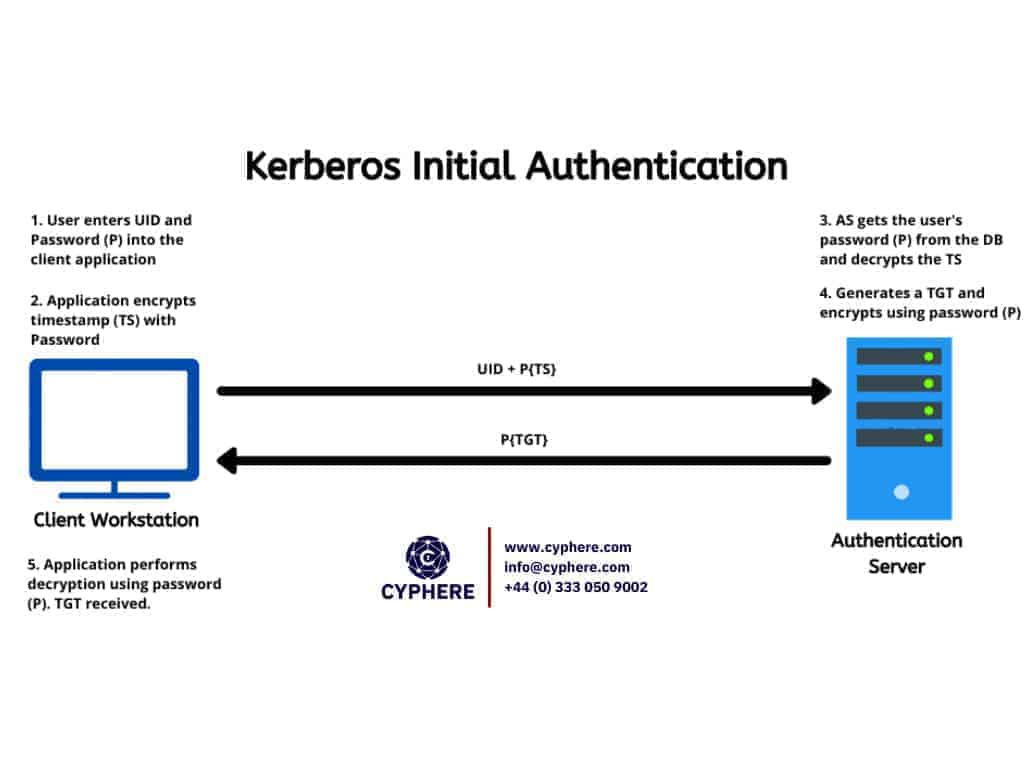
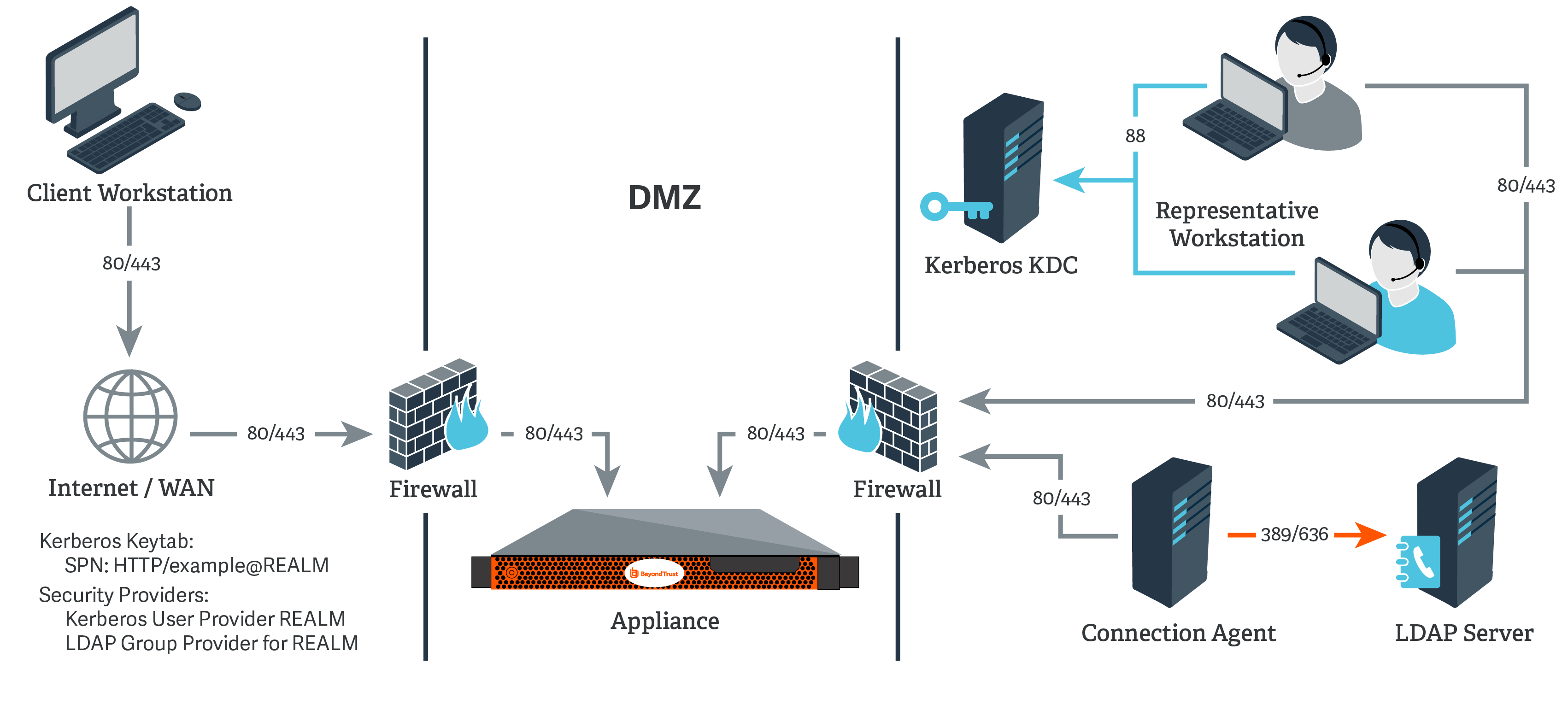
Adding Kerberos realms for discovery authentication - Documentation for BMC Helix Discovery - BMC Documentation

Preparing on-premises and AWS environments for external Kerberos authentication for Amazon RDS | AWS Database Blog

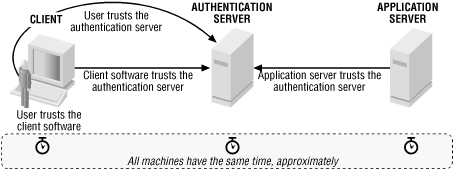
Securing API using Kerberos at the Message Level - Knowledge base - Software AG Tech Community & Forums